BSCP preparation and exam experience
The past 2-3 months, I’ve been spending some time on preparing for the BSCP (Burp Suite Certified Practitioner) certification. I passed the exam and in this post I will share how I prepared, how the exam went and some tips for you to pass the exam.
What is BSCP?
From the Portswigger: “The Burp Suite Certified Practitioner (BSCP) is an official certification for web security professionals, from the makers of Burp Suite. Becoming a Burp Suite Certified Practitioner demonstrates a deep knowledge of web security vulnerabilities, the correct mindset to exploit them, and of course, the Burp Suite skills needed to carry this out. Successfully passing the Burp Suite Certified Practitioner exam indicates a high-level proficiency in web security testing. It is aimed at penetration testers, and the organizations that employ them.”
https://portswigger.net/web-security/certification
The certification is all about web application pentesting. Something I like to do very much. So preparing for the exam wasn’t that much of a punishment :).

Preparing for the exam
Preparing for BSCP is all about practice. Luckily, Portswigger created a lot of labs which you can do for free. https://portswigger.net/web-security/dashboard.
In total there are at the time of writing this post, 269 labs. Portswigger recommends completing all “Apprentice” and “Practitioner” labs. At the time of writing this post, this means completing 230 labs.
Portswigger covers almost all web-based security vulnerabilities in their topics:
1 | SQL injection |
You may ask yourself “Do I need to know all of this?” Well, yes. The exam is meant to be challenging. So what was my take on this? Well, I already am somewhat experienced with web application pentesting prior to preparing for this exam. I gained some knowledge/skills from HackTheBox, TryHackMe, OSCP and real-life pentesting. However, I chose to complete a lot of labs. And I’m glad I did.
By completing most of the labs, especially from the topics that you do not know so much about, you will gain a lot of new information. The content from the labs is excellent, and I do not think there is a better platform to learn these web-based attacks. In total, I completed 69% of the labs by the time I passed the exam: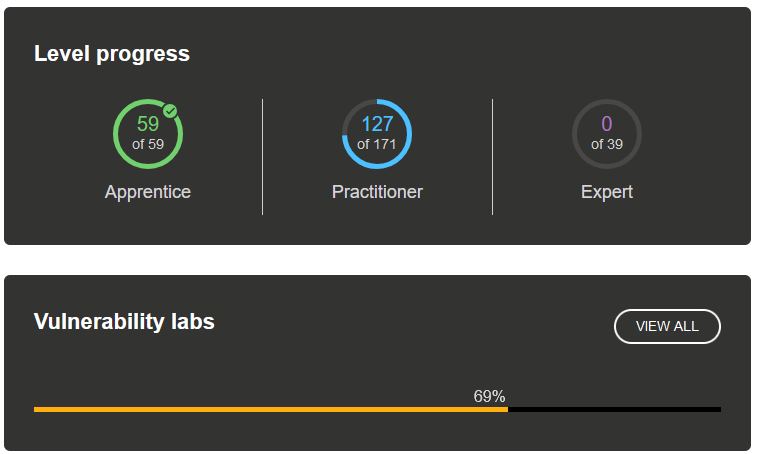
I decided to exercise the topics that I did not know so much about like Request Smuggling, OAuth and prototype pollution. Next to that, I confirmed my knowledge by doing the labs of the topics that I already knew a thing or two about.
Mystery labs
The academy provides a mystery lab environment where you must exploit an unknown vulnerability in a web application, just like in the exam. After completing most of the labs, I made sure to do a lot of these. You can also do mystery labs from each topic. This is nice since you can complete a topic and then do the mystery labs for that specific topic and move on to the next.
Practice exams
Portswigger provides two practice exams which you can do for free, any time you want, as often as you want. I completed both practice exams before taking my exam. They are very comparable to the real exam. The only downside was that they are very similar in the type of vulnerabilities.
Exam
First, let me tell you a bit about the examination process, because it is quite interesting. You will have four hours to complete the Burp Suite Certified Practitioner exam. There are two applications, and each application contains deliberate vulnerabilities. This means that each application can be completed in three stages:
Stage 1: Access any user account.
Stage 2: Use your user account to access the admin interface, perhaps by elevating your privileges or compromising the administrator account.
Stage 3: Use the admin interface to read the contents of /home/carlos/secret from the server's filesystem, and submit it using "submit solution".
While exploiting each application, you will gain access to powerful functionality. If you use this to delete your own account or a core system component, you may make your exam impossible to complete.
There is always an administrator account with the username “administrator”, plus a lower-privileged account usually called “carlos”. If you find a username enumeration vulnerability, you may be able to break into a low-privileged account using the following username list: https://portswigger.net/web-security/authentication/auth-lab-usernames and password list: https://portswigger.net/web-security/authentication/auth-lab-passwords.
More info: https://portswigger.net/web-security/certification/how-it-works#what-the-exam-involves
Doing the exam
I managed to pass my exam on the second attempt. That’s right, the second one. The reason for this was that I did not practice a specific topic enough. However, I have a saying that failure is part of success. Coming back stronger at my second attempt (1 week later than the first attempt), I passed my exam within 2 hours.
On my first attempt, I managed to complete 1/2 web applications within 20 minutes. That means that I had 3 hours and 40 minutes to complete the second one. After completing it within such a fast time, I of course was very confident that I was going to pass. However, the second web application took a revenge on me. It took me very long to identify the vulnerability for initial access.
At the time of identifying the vulnerability, I had about 1 hour and 30 minutes left. I could not exploit it in order to gain initial access within that time. The result: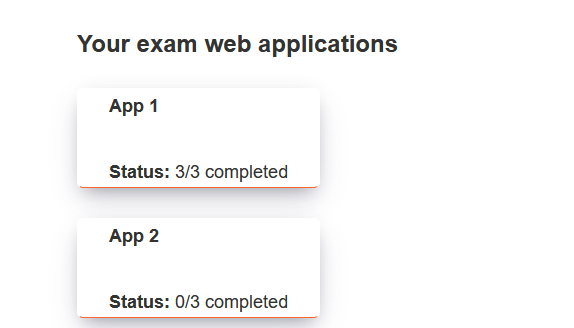
Fortunately, I managed to at least identify the type of vulnerability. Which meant that I was able to practice this topic more and be prepared if it was on the second attempt as well.
On my second attempt I could not identify the vulnerability on the first web application. So I decided to start with the second web application instead. On the second webapp I was able to identify the vulnerability for initial access and quickly exploit it to get access to a user account. I believe my strong side for webapp pentesting are the privilege escalation types of vulnerabilities of the Portswigger exam topics. Because on all the webapps I did, after getting initial access it was game over very quickly. At the time I completed the second webapp, I had about 3 hours to complete the first webapp. Now it was time to get back to the first webapp.
After figuring out that burp suite was probably lying to me because of some false positives on the first application, I went looking for other types of initial access vulnerabilities. Being happy I finally found it, it was game over very quickly for the first webapp as well :).
After completing the exam, you have to upload your .burp file that you should’ve saved. After doing so, Portswigger took 3 business days to do their checks before letting me know I passed the exam!

My review
If you are planning on improving your web application pentesting skills, look no further. BSCP is the certification to do so. I have gained a lot of knowledge and made notes of the attacks involved, which you can b.t.w. find here: https://notes.incendium.rocks/pentesting-notes/web
There is plenty of content for you to be prepared for the exam on the portswigger academy alone. The content is very well explained and applicable on real-life webapps.
The costs for the exam are not expensive at all compared to other certifications. They will cost you $99 or 89 euros (assumed that euro is still worth more at the time of you reading this). However, you will need to purchase a license for Burp Suite Pro in order to pass the exam. This is because you need to provide a .burp file after completing the exam. Also, to complete some labs (and maybe even the exam), you will need the Burp Suite collaborator.
Overall, my experience was very good, and I would recommend this certification to anymore eager to learn more about web pentesting.
Tips to pass the exam
The exam is meant to be challenging. Fortunately, there are some great recourses online that I found particularly useful.
- https://github.com/botesjuan/Burp-Suite-Certified-Practitioner-Exam-Study
- https://github.com/DingyShark/BurpSuiteCertifiedPractitioner
- https://www.youtube.com/watch?v=L-3jJTGLAhc
- Request Smuggling!: https://www.youtube.com/watch?v=4S5fkKJ4SM4&list=PLGb2cDlBWRUX1_7RAIjRkZDYgAB3VbUSw
Other than that here are some general tips:
- Do a lot of mystery labs to learn to identify vulnerabilities & exploit them without prior knowledge about the type of vulnerability.
- Make sure you are comfortable doing all topics.
- Make the exam your own. Think about a methodology that you will use when taking the exam. For example; which types of vulnerabilities can arise in a specific part of the exam? For example, you will most likely not find LFI vulnerabilities before initial access since the end goal is to read the /home/secret/carlos.txt file.
- Read blog posts like mine about the exam
- Read the exam preparation documentation from portswigger carefully.