
Remotely crashing the Spooler service
Showcasing a vulnerability in Windows that causes the Spooler service to crash remotely.

Showcasing a vulnerability in Windows that causes the Spooler service to crash remotely.
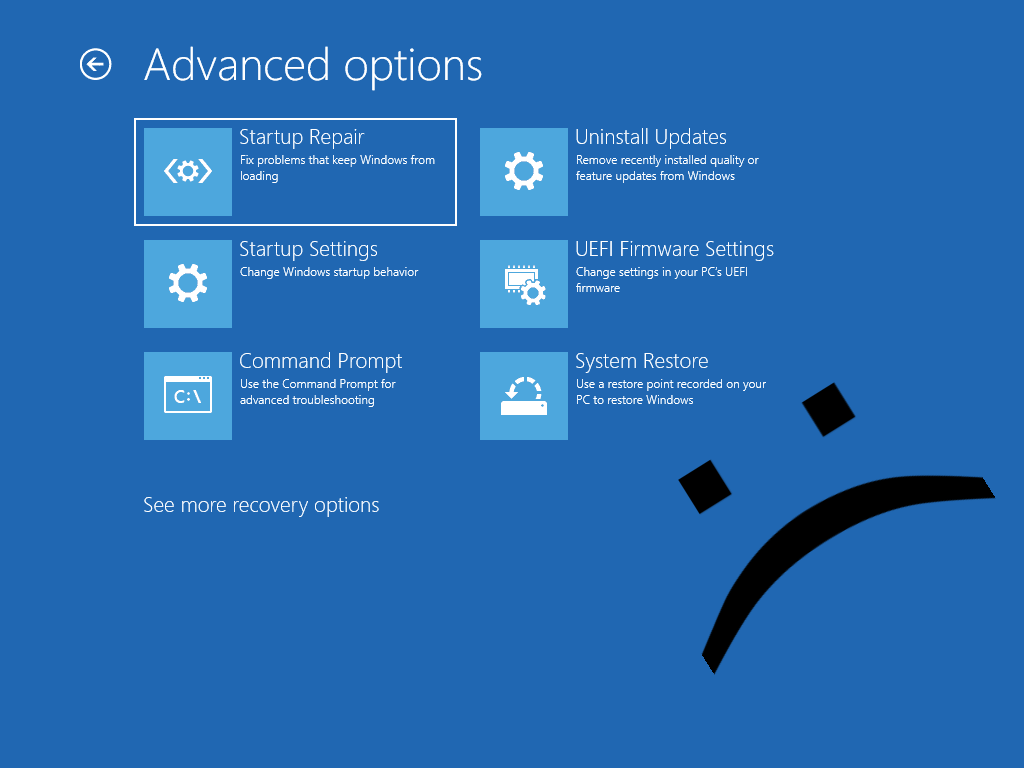
CVE-2025-59253: Demonstrating a vulnerability in Windows that leads to a low privileged user being able to delete the boot configuration data (BCD) through COM.
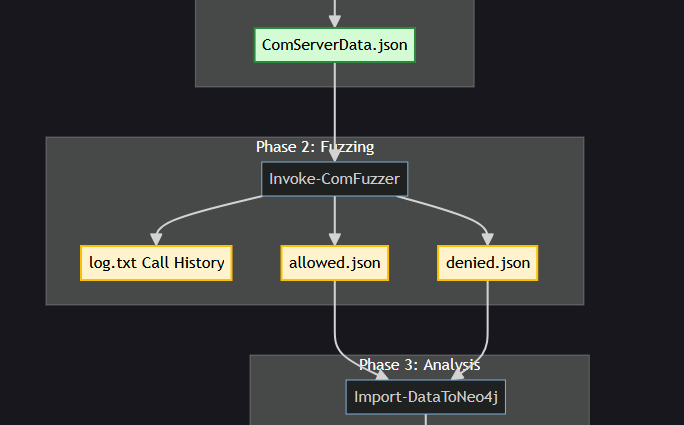
Diving into COM/DCOM and how to automate vulnerability research using a fuzzing approach.
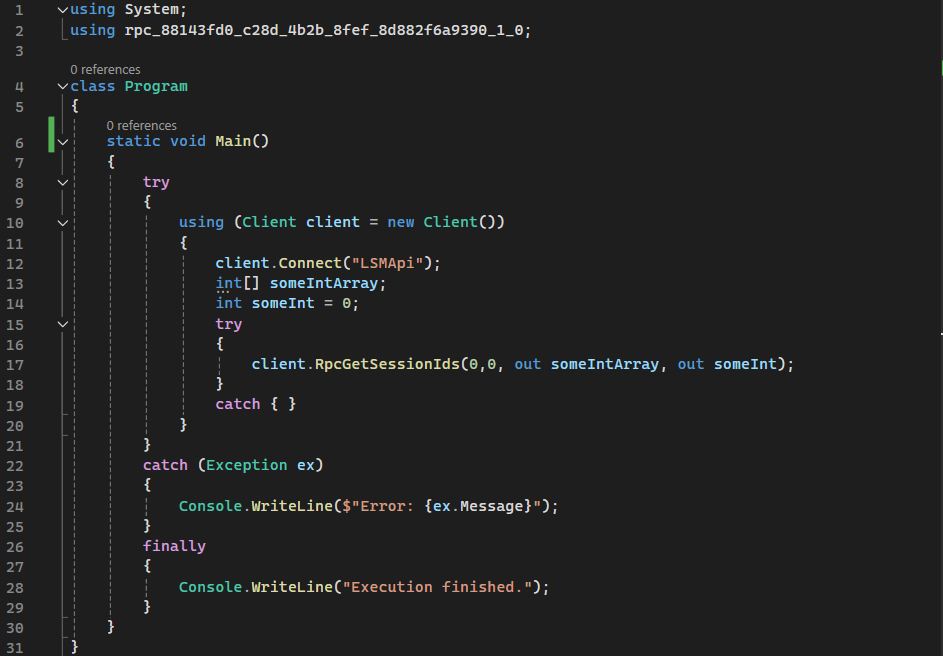
Showcasing some different ways to craft exploits for vulnerabilities over MS-RPC
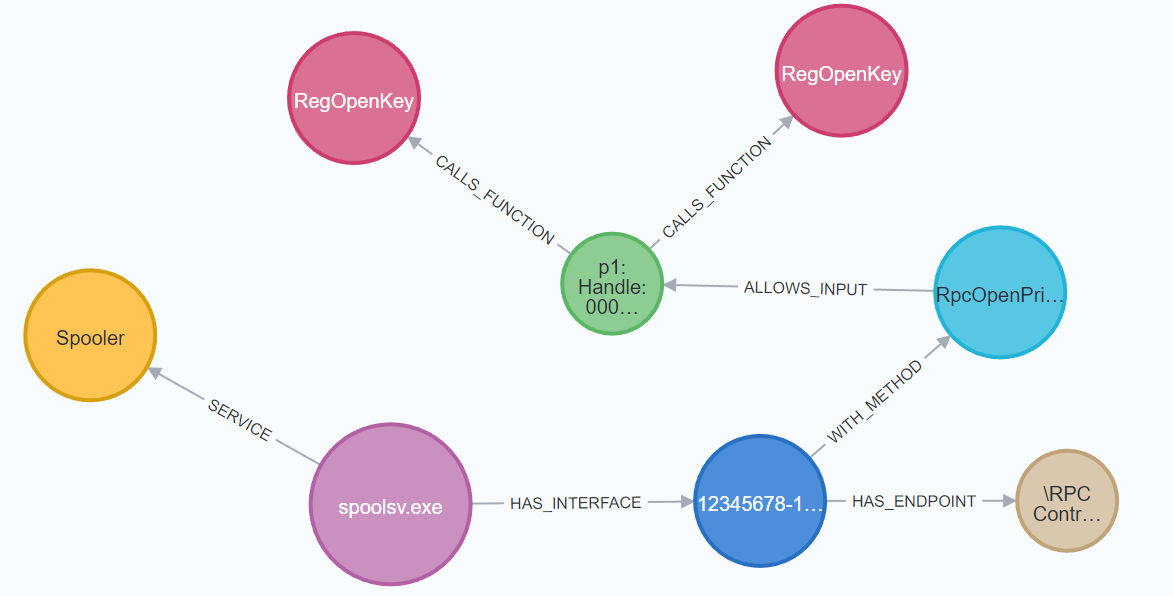
Partially solving the problem for procedures that need valid complex parameter types to fuzz, and open sourcing the tool
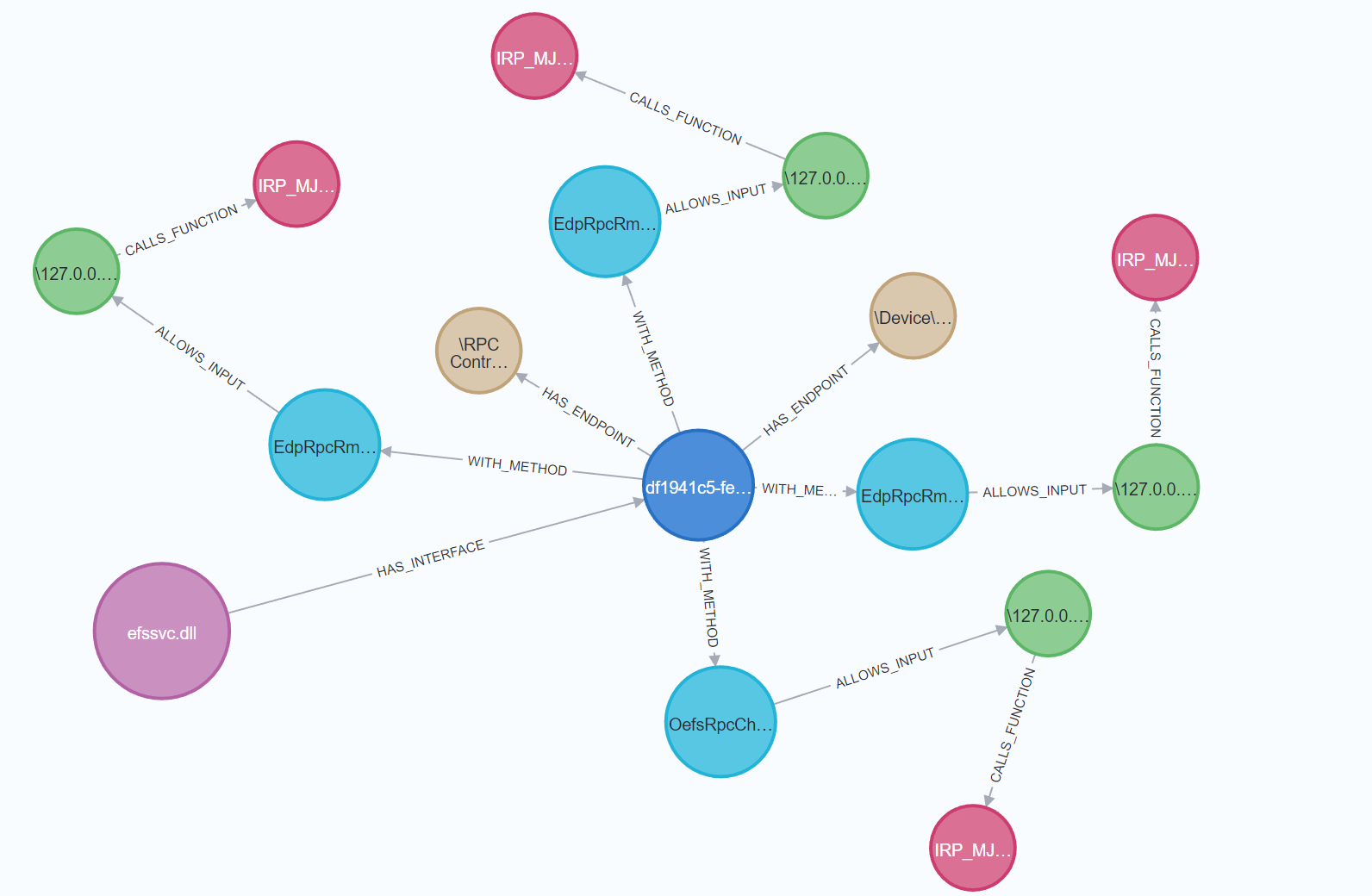
Diving into the MS-RPC protocol and how to automate vulnerability research using a fuzzing approach.

CVE-2025-26651: Revealing a vulnerability in Windows Local Session Manager (LSM), that causes it to crash

Having fun with Pass the Certificate and Kerberos errors and how to work around them

Crashing Windows by exploiting two vulnerabilities in the power service

Using NTLMRelay2self with RBCD and BloodyAD to escalate privileges on a Windows system with LDAPS being blocked on the domain controller.